
Billions of messages are sent every day via real-time messaging apps. From personal chats to workplace collaboration tools – these platforms handle an enormous volume of sensitive information: financial details, private conversations, health data, business IP and many many more.
This convenience, however, comes with a cost. Hackers and malicious actors see chat apps as high-value targets. Data breaches, phishing attacks and privacy violations can destroy user trust overnight. For developers, building secure messaging isn’t optional; it’s the foundation of credibility.
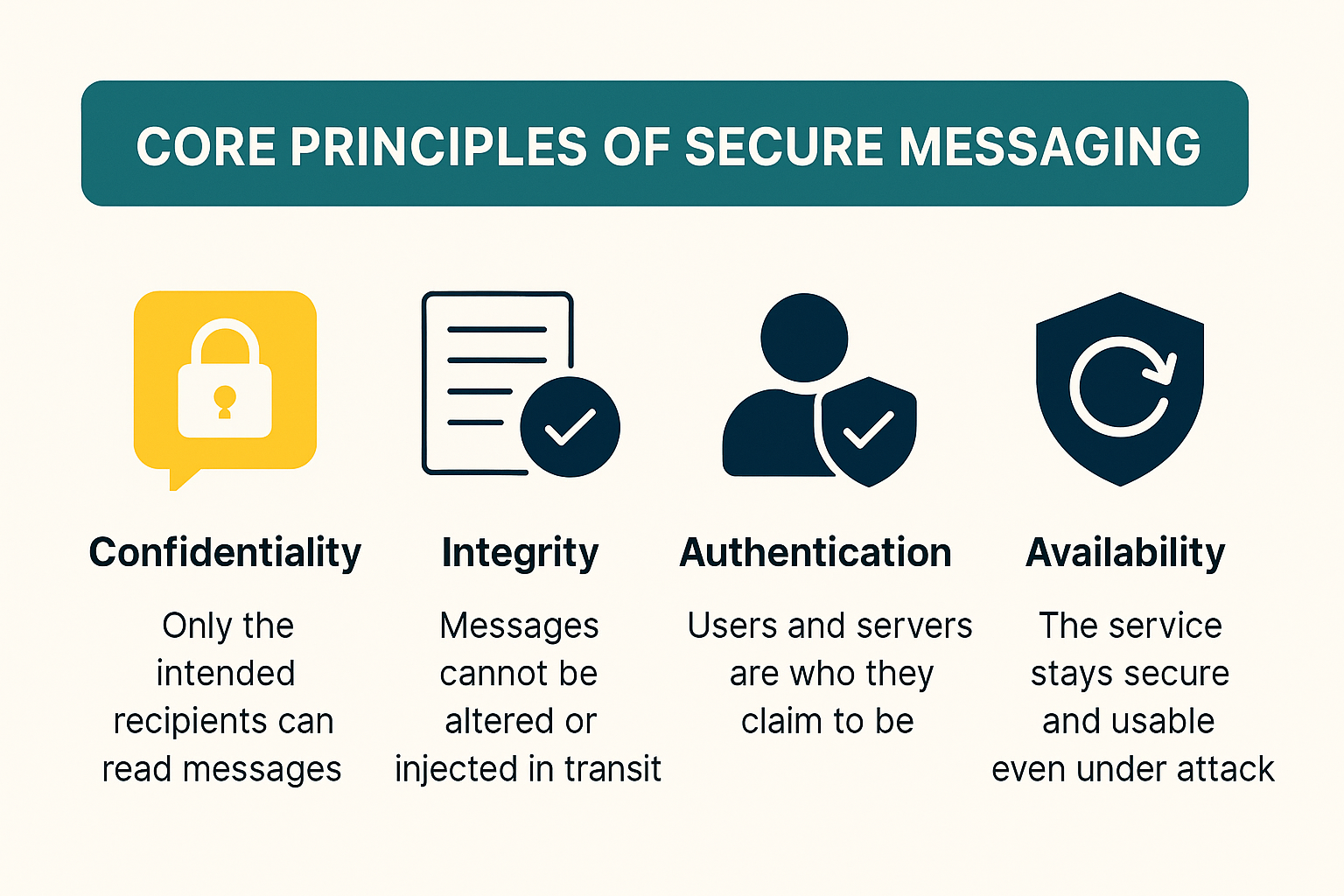
In this article, we’ll explore the essential practices that help developers protect user data in real-time chat applications: from encryption and authentication to storage and compliance.
Security begins with awareness
When users open a chat app, they trust the app with their personal conversations, private photos, or business secrets. That trust can vanish instantly if their data falls into the wrong hands.
To build a truly secure messaging experience, developers first need to understand what they’re protecting against:
-
Eavesdropping & interception – unencrypted traffic can be read or modified during transmission.
-
Man-in-the-middle (MITM) attacks – attackers impersonate servers or clients to intercept data.
-
Unauthorized data access – weak authentication or insecure APIs can expose private messages.
-
Data leaks from misconfigured servers – poorly secured storage buckets or backups can be downloaded by anyone.
-
Insecure push notifications – sensitive content revealed in plain text on a user’s lock screen.
Because chat is instantaneous and often stored in multiple locations (server + client), the attack surface is larger than for traditional apps.
Practical measures to secure user information
1. Implement End-to-End Encryption (E2EE)
E2EE ensures that messages are encrypted on the sender’s device and only decrypted on the recipient’s device. Even the server can’t read the content.
-
Use established protocols such as the Signal Protocol or Double Ratchet for key management.
-
Employ Perfect Forward Secrecy (PFS) to prevent future key compromise from exposing past messages.
-
Don’t roll your own crypto; rely on well-maintained libraries.
If E2EE isn’t feasible for your entire app (e.g., for compliance reasons), at least encrypt data in transit (TLS 1.3) and at rest.
Useful link: https://developers.connectycube.com/guides/security-compliance/
2. Secure authentication & authorization
2.1 Use standards-based authentication (OAuth 2.0 / OpenID Connect)
Don’t reinvent login logic. Use well-tested, open standards for both security and interoperability.
-
OAuth 2.0 -> Ideal for token-based access control between client and API.
-
Use Authorization code flow with PKCE for native and SPA apps to prevent code interception.
-
-
OpenID Connect (OIDC) -> Built on top of OAuth 2.0, adds identity layer for user profiles, useful for cross-app login.
2.2 Enforce strong password & credential policies
-
Require minimum password entropy (length, symbols, no common words).
-
Hash passwords using Argon2id (preferred), bcrypt, or scrypt with a unique salt per user.
-
Rotate salts and rehash passwords when algorithm parameters change.
-
Never store API keys, tokens, or credentials directly in code – use environment variables or secret managers (e.g., AWS Secrets Manager, Vault).
2.3 Multi-Factor Authentication (MFA)
Add an extra layer for sensitive or admin accounts. Options include:
-
TOTP (Time-based One-Time Password) via Google Authenticator or Authy.
-
SMS / Email codes (less secure, but easy to implement).
Use a separate endpoint for MFA verification and rate-limit attempts.
2.4 Token lifecycle & session security
Use JWTs (JSON Web Tokens) or opaque tokens for access control. JWT design recommendations:
-
Include only minimal claims (
sub,iat,exp,scope). -
Keep token lifetime short (5–15 minutes) and issue refresh tokens with rotation.
-
Sign using RS256 (asymmetric) or ES256 (ECDSA). Avoid
noneor symmetric secrets shared across apps. -
Implement token revocation via a denylist or refresh token rotation (store refresh IDs in DB).
-
For mobile/web hybrid apps:
-
Store access token in memory, refresh token in secure storage (Keychain/Keystore).
-
Revoke both immediately upon logout or device change.
-
2.5 Authorization: implement fine-grained access control
After authentication, authorization defines what a user or bot can do. Use one of these patterns:
-
RBAC (Role-Based Access Control) – assign roles (
user,moderator,admin) and validate permissions per API route. -
ABAC (Attribute-Based Access Control) – check rules based on context (user attributes, message ownership, resource type). Useful for multi-tenant chat apps.
- PBAC (Policy-Based Access Control) – define policies as JSON or YAML (e.g., using Oso or Casbin).
For multi-tenant systems, always include a tenant ID claim in tokens and verify it on every request to isolate user data.
2.6 Protect session cookies & websockets
-
Use
SameSite=strictandSecureflags for cookies. -
Always serve authentication endpoints via HTTPS.
-
When using WebSockets, authenticate the initial handshake with a JWT or API key, and periodically re-validate the session.
2.7 Monitor and audit authentication events
-
Log login, logout, and failed attempts (anonymized, no raw passwords).
-
Detect unusual patterns – multiple logins from different IPs, token reuse, expired refresh token usage.
-
Implement rate limiting (e.g.,
express-rate-limitor Cloudflare Rules).
3. Protect data storage & transmission
Even with end-to-end encryption, certain metadata (timestamps, message IDs, device info, presence data) will still reach your servers and must be protected as carefully as message content.
-
Encrypt at rest – use AES-256-GCM or ChaCha20-Poly1305 for all stored data, including message history, attachments, and user profiles. Apply full-disk encryption on servers and encrypt database backups separately.
-
For PostgreSQL or MongoDB, use built-in TDE (Transparent Data Encryption) or an external layer such as HashiCorp Vault or AWS KMS.
-
Regularly rotate encryption keys and maintain a versioned key store to support decryption of older records when necessary.
-
-
Encrypt in transit – enforce TLS 1.3 with strong ciphers (e.g.,
TLS_AES_256_GCM_SHA384) for all HTTP, WebSocket, and file-upload endpoints.-
Use HSTS headers to prevent protocol downgrade attacks.
-
Disable weak protocols (TLS 1.0/1.1) and ciphers like RC4 or 3DES.
-
-
Key management – store cryptographic keys separately from data using a Hardware Security Module (HSM) or cloud key vault (AWS KMS, Azure Key Vault, GCP KMS).
-
Implement key access policies – only backend services that require decryption should have read permissions.
-
Log and audit all key usage operations.
-
-
Data retention & anonymization – define retention policies per data type (e.g., messages = 30 days, logs = 90 days).
-
Use background jobs to purge old records or pseudonymize user IDs in archived analytics.
-
Ensure deletions cascade to backups and CDN caches.
-
-
Integrity & verification – add checksums (SHA-256) or digital signatures to verify file integrity during uploads/downloads.
-
For large media, generate signed URLs that expire within minutes to restrict unauthorized access.
-
These measures ensure that even if your network or storage is compromised, attackers cannot read or tamper with user data without access to protected encryption keys.
4. Secure APIs & SDKs
Most chat platforms expose REST or GraphQL APIs for message delivery, file handling, and user management and often distribute SDKs to simplify access. Every exposed interface increases the attack surface, so API and SDK hardening is essential.
4.1 Input validation and sanitization
All inbound data should be treated as untrusted, even when it comes from your own mobile client.
-
Use server-side validation frameworks such as Joi (Node.js), class-validator (NestJS), or Marshmallow (Python).
-
Always whitelist expected fields instead of blacklisting bad ones.
-
Escape or sanitize user-supplied input to prevent injection vulnerabilities (
SQLi,NoSQLi,XSS). - Use parameterized queries for database access and ORM parameter binding.
4.2 Authentication & token validation
-
Require a valid access token (JWT or OAuth) on every request, even for WebSockets.
-
Use signature verification (RS256 / ES256) and reject unsigned or malformed tokens immediately.
-
Implement token introspection or cache validation results in Redis to prevent replay attacks.
-
For long-lived connections (like chat WebSockets), periodically re-authenticate with a short-lived session token.
4.3 Rate limiting and abuse prevention
To protect your API from brute-force attacks or spam:
-
Apply rate limits per IP + user + endpoint, using sliding windows or token buckets (e.g.,
express-rate-limit, NGINXlimit_req, or API Gateway throttling). -
Combine with CAPTCHA or Proof-of-Work for public endpoints (e.g., signup or anonymous messaging).
-
Detect and block patterns like message floods or bot-driven socket spam in real time.
4.4 Use signed URLs for file handling
File uploads and downloads are common vectors for data leaks.
-
Generate time-limited signed URLs with embedded cryptographic signatures (e.g., AWS S3 pre-signed URLs, Google Cloud Signed URLs).
-
Restrict MIME types (
image/*,video/*) and set file size limits. -
Scan uploaded files asynchronously with ClamAV or third-party malware scanners.
-
Store uploaded files in isolated buckets and never expose raw storage paths.
4.5 Secure CORS and API exposure
-
Set strict CORS headers:
-
Never use
Access-Control-Allow-Origin: *for endpoints that require authentication. -
For public APIs, expose only necessary routes, and separate admin or internal APIs onto different subdomains (
api.connectycube.comvs.internal.connectycube.net).
4.6 SDK security best practices
If you distribute SDKs to external developers:
-
Abstract authentication – make the SDK handle token refresh and HTTPS enforcement by default.
-
Disable any debug or test endpoints in production builds.
-
Embed runtime checks to prevent sending unencrypted HTTP requests.
-
Sign SDK releases and verify package integrity (npm
integrityhashes orpipsignatures). -
Clearly document secure usage patterns (e.g., “never log tokens” or “always handle errors securely”).
4.7 Logging, monitoring & versioning
-
Log every API call with anonymized user IDs and trace IDs (use OpenTelemetry).
-
Implement API versioning (
/v1,/v2) to deprecate outdated or insecure endpoints safely. -
Use WAFs (Web Application Firewalls) like AWS WAF or Cloudflare to detect anomalies automatically.
5. Handle push notifications carefully
Push notifications are convenient for real-time engagement but pose significant security risks if implemented incorrectly. They often cross third-party infrastructures (APNs, FCM, Huawei Push Kit), so sensitive data should never travel in plaintext through these services.
5.1 Never include sensitive message content in payloads
Push notification payloads can be intercepted, logged or shown on lock screens – meaning sensitive content could be exposed even without unlocking the device.
Instead, do the following:
-
Send generic or obfuscated notifications
-
The client then uses the included IDs to securely fetch the full message from your backend using an authenticated API call (with JWT or session token).
-
On the server, validate that the user requesting the message is a participant in that conversation before returning the content.
5.2 Token-based authentication for message fetching
When the app opens or receives a background event:
-
Use a short-lived access token (JWT with ≤15-minute lifetime) to fetch the actual message content via HTTPS.
-
Never store or transmit refresh tokens in notification handlers.
-
On the backend, implement audience-based validation to ensure the token’s
submatches the intended message recipient.
5.3 Use “silent” or “background” notifications for syncing
Both Android and iOS allow non-visible push types that trigger background data syncs.
This is ideal for secure apps: the OS wakes the app silently, allowing it to fetch data over encrypted channels.
-
iOS (APNs):
-
Use
"content-available": 1in the payload. -
Don’t include the
alertfield – this makes the push silent. -
Ensure your app has the background modes -> remote notifications capability enabled.
-
Fetch data using a secure HTTPS request with a short-lived token.
-
- Android (FCM):
- Use
data-only messages (nonotificationkey) so the app can handle them silently in the background. - Implement background fetch logic inside a
FirebaseMessagingService.
Firebase information is here: https://firebase.google.com/docs/cloud-messaging/
- Use
5.4 Encrypt payloads for highly sensitive use cases
If you must send partial message data in the notification (for example, to show previews in enterprise messaging), encrypt the payload at the application level:
-
Encrypt message content with a shared symmetric key per conversation using AES-GCM or ChaCha20-Poly1305.
-
Store the symmetric key securely in device keychain/keystore and never on the server.
-
Decrypt on-device after receiving the push
- Rotate encryption keys periodically and re-establish during session reauthentication.
5.5 Control visibility and logging
-
Avoid exposing message content in OS logs, analytics, or crash reports.
-
For iOS, set
UNNotificationPresentationOptions.nonefor background updates that don’t need to appear visually. -
For Android, use notification channels with
VISIBILITY_PRIVATEorVISIBILITY_SECRETto hide notification text from the lock screen.
5.6 Verify delivery and prevent replay attacks
-
Generate unique message identifiers (
UUIDv4) for each notification. -
Validate each delivery once on the backend; reject duplicates to prevent replay or spam.
-
For high-availability systems, store recent notification hashes temporarily (e.g., Redis) and verify HMAC integrity before processing.
This implementation ensures that push notifications enhance UX without compromising privacy or security, even when passing through untrusted third-party channels.
6. Privacy by design & compliance
Privacy regulations like GDPR (EU), HIPAA, CCPA (California), PIPEDA (Canada), and LGPD (Brazil) impose strict technical and operational rules for how user data is collected, stored, processed, and deleted. For messaging apps, where sensitive content is exchanged in real time, compliance is not just a legal checkbox – it directly influences how you design your backend, APIs, and data flows.
6.1 Data minimization & purpose limitation
Collect only what’s essential for the chat to function. Every new field in your database should have a documented purpose.
Implementation guidelines:
-
Use strict schemas in your database models (Mongoose, Prisma, Sequelize) – reject fields not defined in the schema.
-
Avoid logging personally identifiable information (PII) such as full names, phone numbers, or email addresses in plaintext logs.
-
Anonymize telemetry and analytics data by replacing user IDs with random UUIDs or salted hashes.
- Use data classification tags in your code or DB to separate personal from non-personal data.
6.2 Explicit consent management
Before collecting or processing personal data (like contact lists or location), obtain clear user consent and store the record of it.
Implementation details:
-
Add a
consent_statusfield to yourUserstable with timestamps and consent versioning (accepted_v3,revoked_v4). -
Present a modal or screen explaining what data is collected and why (don’t hide it in Terms & Conditions).
-
Keep consent records auditable — log changes in a secure audit table or use an immutable ledger (e.g., AWS QLDB).
-
Expose an API to revoke consent at any time
6.3 Right to access, portability, and erasure
Users have the right to request all their data or to have it deleted (“right to be forgotten”).
Developer requirements:
-
Data Access API – expose a secure endpoint (authenticated with MFA) to export all user-related data (messages, files, settings) as JSON or ZIP.
-
Data erasure workflow:
-
Use asynchronous jobs (e.g., with BullMQ or Celery) to delete all user-related data from primary DBs, caches, and file storage.
-
Soft-delete first, then purge after verification.
-
Cascade deletions through relationships (
ON DELETE CASCADEor manual cleanup). - Remove associated media from S3/GCS using signed admin credentials.
-
- Portability – allow export in machine-readable format (JSON, CSV, XML) following GDPR Article 20.
6.4 Data retention & expiry policies
Define how long user data and messages are stored. Set automatic deletion or anonymization schedules.
How to implement:
-
Add a
created_attimestamp to all stored records and run a cron job that deletes or anonymizes data after retention expires. -
Use TTL indexes (Time-To-Live) in MongoDB or partition pruning in PostgreSQL to automate cleanup.
- Document these policies in your privacy policy and ensure your API follows them consistently.
6.5 Data localization & residency
Some laws (like GDPR) require data to be stored within specific geographic regions.
Technical setup:
-
Use region-based databases or clusters (e.g., AWS RDS Multi-Region, GCP Spanner).
-
Store region info with each user record (
user.region = 'eu') and route traffic accordingly via load balancer or API gateway. -
Encrypt backups separately for each region with different keys.
6.6 Secure data processing & logging
-
Avoid storing raw chat content in logs.
-
Mask sensitive values in logs and monitoring tools (
user@example.com->u***@example.com). -
Use centralized logging systems (ELK, Loki, CloudWatch) with access controls and data retention limits.
-
Pseudonymize analytics and crash reports (e.g., by using hashed user IDs).
6.7 Privacy auditing & compliance automation
-
Maintain a Data Processing Inventory: a JSON or YAML file listing all collected fields, storage locations, and purposes.
-
Implement privacy unit tests – automated tests that ensure no unexpected PII fields are logged or returned via APIs.
-
Use tools like Datadog Sensitive Data Scanner, AWS Macie, or GitGuardian to detect exposed secrets or personal data.
-
Regularly perform Privacy Impact Assessments (PIA) and document all data flows.
6.8 Encryption & access controls
Compliance frameworks require protecting PII both at rest and in transit:
-
Encrypt all PII columns (
email,phone,IP) using field-level encryption or KMS-managed encryption keys. -
Apply role-based access control (RBAC) – only allow privileged services or admins to query sensitive fields.
-
Log every access to PII for audit purposes.
Useful link: https://medium.com/@connectycube/connectycube-shares-its-ways-to-gdpr-compliance-4ff5a4a29f64
Principles of Building Secure Messaging in ConnectyCube
At ConnectyCube, we follow a security-first architecture – every component from SDKs to cloud infrastructure is designed to protect user data and communication privacy.
All messaging traffic is encrypted end-to-end using modern cryptography standards (AES-256, RSA-2048). Authentication relies on JWT tokens with short lifetimes, while all API and WebSocket connections are secured with TLS 1.3. Messages, attachments, and backups remain encrypted at rest, and file uploads use signed URLs that expire automatically.
Data privacy and compliance are built in. ConnectyCube adheres to GDPR / CCPA, allows data export or deletion on demand, and provides configurable retention policies. Keys are securely managed and rotated within internal KMS systems, and infrastructure isolation (shared, dedicated, or on-premise) ensures full control over data location.
In practice, ConnectyCube applies:
-
End-to-end message encryption
-
Secure token-based authentication
-
TLS-encrypted APIs and SDKs
-
GDPR-compliant data handling
-
Regular key rotation and monitoring
By choosing ConnectyCube, you can be confident that every message, call, and file transfer is protected by enterprise-grade security measures, so your users’ data stays private, your app remains compliant, and your platform earns lasting trust.
Explore more on secure messaging
Secure chat: implementing end-to-end encryption in Web and React Native chat apps
Secure chat: implementing end-to-end encryption in Flutter chat apps
Implementing End-to-End Encryption in Flutter Chat Apps: A Guide to Secure Messaging
Introducing enhanced GET Users API V2: A Leap Forward in Security
Encrypted Push Notifications in React Native
Introducing Advanced Features: Encrypted Address Book
Conclusion: security is an ongoing commitment
Protecting user data in a real-time chat application is an ongoing commitment. Threats evolve, and so must your defenses.
By following best practices described in this article you can drastically reduce risk and build user trust. The key is to make security part of your product DNA from day one. Your users’ privacy and your reputation depend on it.
If security and privacy are priorities for your app, ConnectyCube is built for you. Sign up now to get a secure backend for chat, voice, and video – so you can focus on features while we handle the protection.
—
Join the ConnectyCube Discord сommunity for quick answers and expert tips.

